Active Directory (AD) is a renowned service by Microsoft, known to many organizations for its network management functions and access control. We can make the most out of it by understanding how AD works – so let’s explore its different features in order to gain full knowledge on this powerful tool!
Uncovering What is Active Directory (AD)
Active Directory (AD) is a comprehensive directory service developed by Microsoft, designed primarily to handle active directory sites. It administers network resources and user access in an organized manner, helping strengthen security while providing centralized control of computer & user rights as well as facilitating single sign-on for collaborative objectives via Group Policy configurations.
Essence of Active Directory Domain Services (AD DS)
Domain Services (AD DS) is a component of Microsoft Active Directory that provides network administrators with numerous capabilities, including authentication, authorization, access control and the ability to manage user rights. AD DS also offers supplementary services such as Single Sign-On (SSO), security certificates and LDAP which help bolster its overall efficiency in network management. Its key roles are granting users access to resources on the associated system while administering group policies within an organization. These abilities make it a necessary part of any enterprise’s digital infrastructure.
The Role of Domain Controllers
Domain controllers are essential for any Windows Server domain, providing physical storage for the AD database and managing user authentication. They perform various Active Directory tasks to authorize users based on their account information stored in the directory. When a user attempts access to resources within an active directory domain, Domain Controllers will validate credentials against this data before granting permission by creating security tokens containing SIDs (security identifiers).
Anatomy of Active Directory’s Hierarchical Structure
The hierarchical structure of Active Directory is an example of its carefully-planned and effective design. It consists of domains, trees, and forests, all components that help in managing network resources within the system. Forests act as the topmost logical containers which provide a security boundary while also organizing various objects such as users or devices throughout a connected namespace.
AD’s organization offers several benefits including enhanced organizational efficiency due to centralized administration, improved safety with delegation authority features, and access to Global Catalogs for easy lookup operations on different elements like domain names across multiple directory servers being enabled by this hierarchy’s presence.
Ultimately, AD provides reliability via its hierarchical architecture where each component contributes towards resource management within networks along with creating secure boundaries at higher levels through use cases such as forest optimization used therein predominantly even today globally when it comes to structured IT systems backed up Active Directory solutions.
Organizational Units and Their Significance
Organizational Units (OUs) are a key part of the hierarchical structure in Active Directory, serving as containers for organizing various objects. The use of OUs allows administrators to group elements based on different criteria such as job function, location or organizational infrastructure, making network management more efficient and convenient. Applying Group Policies directly at an OU level offers advanced control capabilities that set it apart from other types of generic AD containers. This makes them very useful tools for IT personnel managing networks.
Understanding Active Directory Objects
Active Directory Objects are the base components of the AD environment and encompass a wide range of entities, for instance active directory users, groups, devices along with other resources. Every object has its own specific attributes like names or passwords that can be recognized by their GUID (Globally Unique Identifier) and SID (Security Identifier). User objects have additional characteristics such as department data email address last logon time group membership etc. Device objects contain information regarding this type of resource’s unique features. Lastly, both types of entities rely on GUIDs/SIDs to offer distinct identification. To define authority within domain limits while controlling access rights too all available assets.
Navigating through Other Active Directory Services
Active Directory Lightweight Directory Services (AD LDS)
AD LDS is a version of AD DS that utilizes the Lightweight Directory Access Protocol (LDAP) and operates as a service on Windows Server. It provides directory services independent from domain-oriented functionalities, providing versatility in different deployment scenarios. In particular, it can be used to offer white page directories for users, bolster security applications and function as an external policy store for apps. As such, this streamlines variant makes available numerous opportunities previously unavailable with other directory services solutions, including those offered by AD DS itself.
Enhancing Security with Active Directory Rights Management Services (AD RMS)
Rights Management Services (AD RMS) is an advanced package of server tools for Windows Server management. It’s purpose is to provide information rights management through encryption, certificates and authentication so as to restrict document access activities performed by authorized personnel including: viewing, editing, copying, saving and printing across multiple formats.
The implementation of AD RMS helps bolster the security environment within a corporation due to its capabilities that consist in encrypting sensitive data. Regulating usage both inside & outside the organization. Obstructing unauthorized entries along with guaranteeing only permitted users are able to get admission or make alterations to documents content. There exists selective functionality denial which limits operations on secure files plus restricting who has access to them. This set of traits goes about ensuring that the safety measure associated with corporate records keeping remains under administration control at all times.
By relying on elements like encryption coupled with functions restrictions placed on legitimate memberships provides enough defense against unauthorized handling involving critical company particulars hence protect delicate documentation via being accessed unlawfully.
Simplifying Sign-On with Active Directory Federation Services (AD FS)
Active Directory Federation Services (AD FS) provides seamless integration with existing Active Directory setups by creating a streamlined Single Sign-On process and implementing centralized identity management. Through this service, users can access various applications through one set of credentials rather than having to continuously input their information. AD FS also validates user identities utilizing claims from trusted tokens for secure resource access without the need for repetitive verification entries. It facilitates federation between partners while offering an enhanced cyber security solution in order to fully incorporate authentication processes across organizational boundaries.
Integrating Cloud with Azure Active Directory
Azure Active Directory (Azure AD) is a cloud-based version of Microsoft’s well known on-premise directory service, allowing identity management for any kind of connected application or service. The Azure AD Connect tool allows users to integrate their existing Active Directory systems with Azure, providing streamlined Single Sign On (SSO) access and Multi Factor Authentication capabilities. This makes the platform highly attractive for modern businesses who wish to benefit from an easy SSO experience while managing identities in both their physical and digital world together. It also offers lifecycle management solutions that are sure to meet most organizations’ needs today, making it indispensable when optimizing IT services across all platforms utilizing Azure Ad technologies!
Syncing On-Premise with Azure: The Role of Azure AD Connect
Azure AD Connect is a Microsoft program intended for local use. It supports the synchronization of user accounts, groups and credentials from on-premises Active Directory to Azure AD. This tool enables users to access both their online and offline resources with only one sign in experience by creating a hybrid identity solution.
The setup process of Azure AD Connect involves launching the installation, linking up with Azure AD, configuring all synchronizing settings then starting off the synchronization procedure eventually. Having this application helps organizations connect objects stored locally on an active directory domain server to cloud services provided through Azure ads, which subsequently would provide secure authentication as well as easy control over either premises based or internet assets associated with those particular user accounts easily accessible at anytime needed quickly.
This important resource ensures consistency between data residing within these two distinct systems allowing automated bi-directional transmission also preserves passwords when moving across servers too while keeping that singular unified login experience safe, reliable & continuously usable without any hitches all around great!
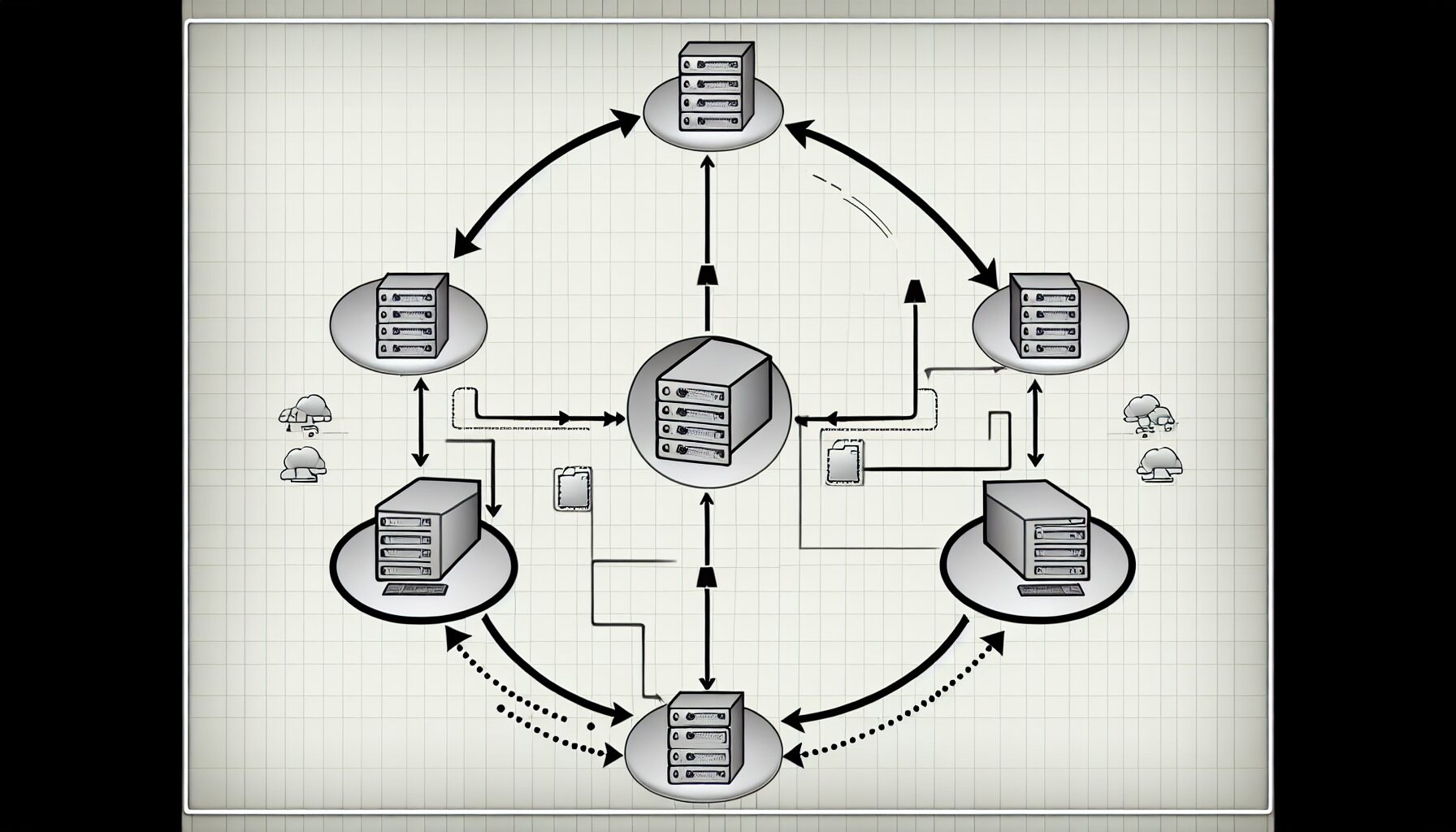
Active Directory Under the Hood: Database and Replication
The Active Directory database is based on the Extensible Storage Engine (ESE98), which has a limit of 16 terabytes and 2 billion objects. There are up to 1 billion security principals in each domain controller’s AD database, divided into partitions with different object types that follow specific replication processes. Replication between domain controllers happens often through Remote Procedure Calls over IP for data synchronization purposes. This way changes made on one Domain Controller will be seen across all other Domain Controllers so as to maintain consistency.
The Structure of the Active Directory Database
The Active Directory database is composed of several segments, each allocated for a unique replication scope and storing objects of distinct kinds. The partitions consist of: domain partition, configuration partition, schema partition and application partition.
Within every segment resides directory data arranged in an orderly pattern that allows the efficient management of information like users groups computers and organizational units as well as enabling their replication through the domain controller stored inside it.
This organized structure plays a crucial role in making sure that the overall performance level within this type of infrastructure isn’t compromised.
Ensuring Consistency with AD Replication
Active Directory replication is a procedure that ensures the transmission and updates of Active Directory objects from one domain controller to another in order to maintain data consistency across multiple controllers on the network. This process follows multi-master replication, which allows every domain controller connected with this setup to be able to change information within its database and send out these changes instantly for other controllers’ use. A variety of components make sure that AD databases are always up-to-date: KCC (Knowledge Consistency Checker), DSA (Directory System Agent), ESE (Extensible Storage Engine) as well as RPC (Remote Procedure Call). Together they facilitate proper synchronization between all related directory items over any number of linked devices so that accuracy remains intact.
Managing Active Directory: Tools and Practices
Effective management of Active Directory requires the use of multiple tools and techniques. One of these is Group Policy, an infrastructure within AD that empowers admins to design exact configurations for users/computers, control security settings, and deploy software packages. Manage user preferences as well as block access to some resources. By using this tool appropriately it makes network administration easier while also guaranteeing uniformity across networks.
The upkeep and enhancement of Active Directory are key components in its oversight too – such best practices include adopting a model based on least-privilege authorization, setting up robust passwords, deleting outmoded accounts regularly, and keeping track/managing issues occurring with respect to AD actively. User profiles should be routinely assessed and adjusted where required along with verifying & modifying rights associated with them correctly so that all these pieces fit together seamlessly under supervision without any risks or delays being encountered by staff members involved.
Leveraging Group Policy for Network Administration
Group Policy is a very powerful tool in Active Directory that can be used to set and enforce policies on users, groups, or computers. This centralized system allows network administrators to easily manage settings for all the entities within their domain with Group Policy Objects (GPOs).
These GPOs are created and assigned either directly to organizational units (OUs) or across an entire domain by allowing control over different aspects of user behavior. The implementation of this policy simplifies efficient administration while also increasing overall security levels.
Overall it offers an effective way to centrally administer systems through regulations imposed at each level specified by these group objects, making management easier as well as more secure than ever before!
Directory Maintenance and Optimization
The active directory environment requires regular maintenance and optimization to function effectively. There are numerous tools available for this purpose, like AlbusBit AD Administrator, CjWdev AD Tidy, Spiceworks People View or Microsoft AdRestore & Windows PowerShell. Optimizing the Active Directory has several benefits such as smaller database size which leads to faster query times, better security settings, and recovering of disk space & defragmentation. Scheduling routine activities with monitoring is essential when automating tasks using scripts/tools keeping the functioning state strong all throughout.
Summary
Active Directory has made a big impact on how organizations administer their network resources, permissions and access. Its hierarchical system combined with the array of services offers an efficient resolution for managing networks. This includes the key components like Active Directory Domain Services (AD DS), Lightweight Directory Services (AD LDS), Rights Management Services (AD RMS) and Federation Services (AD FS).
With cloud computing expanding rapidly, Azure Active Directory emerged as a result of adapting AD into this realm – thus introducing synchronization between local AD to Azure through AZure Connect, which ensures one single sign-on experience. The resilient database structure. To replication process guarantee data consistency throughout all domains operated by directory services such as domain service ads etc. With proper practice management tools can optimize administration making it easier than ever before!
Frequently Asked Questions
How does Azure AD Connect facilitate the integration of on-premises Active Directory with Azure Active Directory?
Azure AD Connect provides a unified approach for connecting your on-premises Active Directory to the Azure Active Directory, allowing organizations to quickly and securely leverage single sign-on functionality so that users can easily access all of Microsoft’s cloud services such as Office 365.