What is encryption, and why is it so crucial for data security? Encryption converts readable information into an unreadable format, ensuring that sensitive data remains private and secure. From protecting your credit card details online to securing corporate data, encryption is essential. This article explains how encryption works, the different types available, and the key benefits it offers.
In This Article:
- Understanding Encryption
- How Encryption Works
- Types of Encryption
- Common Encryption Algorithms
- Benefits of Using Encryption
- Challenges and Limitations of Encryption
- Applications of Encryption
- Key Management in Encryption
- Detecting Encrypted Threats
Key Takeaways
- Encryption secures sensitive data by converting plaintext into ciphertext, ensuring confidentiality and preventing unauthorized access.
- There are three primary types of encryption: symmetric (using a single key), asymmetric (using a key pair), and Advanced Encryption Standard (AES), each serving distinct security purposes.
- Effective key management is essential for maintaining encryption security, involving the secure generation, storage, rotation, and retirement of cryptographic keys.
Understanding Encryption
Data encryption transforms clear, readable information into a scrambled format known as ciphertext using complex algorithms. This process requires a decryption key for anyone wishing to convert the data back into its original form, thereby safeguarding sensitive data from being intercepted and understood by unauthorized parties.
In contemporary digital security practices, encryption is instrumental in protecting sensitive information against cyber threats and illicit access. It accomplishes this through providing confidentiality, ensuring only authorized individuals can access the information, maintaining integrity by preventing tampering with the data, and authenticating user identity. And guaranteeing non-repudiation so that actions cannot be denied later. Encryption underpins online financial transactions like credit card use during internet purchases and helps enterprises maintain customer privacy while adhering to legal regulations designed to prevent expensive breaches of secure data.
Beyond personal protection efforts, encryption serves as an essential element of broader cybersecurity strategies. It secures confidential communications by rendering them unreadable without proper authorization—thwarting attempts at theft or alteration—and plays a pivotal role in securing corporate secrets and other critical assets for both private citizens and business entities alike. A deeper understanding of how encryption works illustrates its importance in reinforcing individual rights to privacy while preserving the integrity of our digital exchanges on various platforms.
How Encryption Works
Modern encryption methods utilize sophisticated algorithms to convert plaintext into an encrypted format known as ciphertext. This process renders the data unreadable, transforming it into a seemingly random sequence of characters that bear no resemblance to the original text without a matching decryption key.
To restore the encrypted data back to its understandable form, one must possess the correct decryption key, typically created by the same algorithm used for encrypting. This ensures a secure and precise reversal from ciphertext back to readable content. The difficulty of deciphering this encoded information without the proper key underscores modern encryption’s effectiveness in safeguarding data.
The processes of encryption and decryption play an essential role in securing sensitive information against unauthorized access or tampering, thereby maintaining its confidentiality and integrity. Consequently, organizations are required to employ robust encryption methods when handling such critical data effectively.
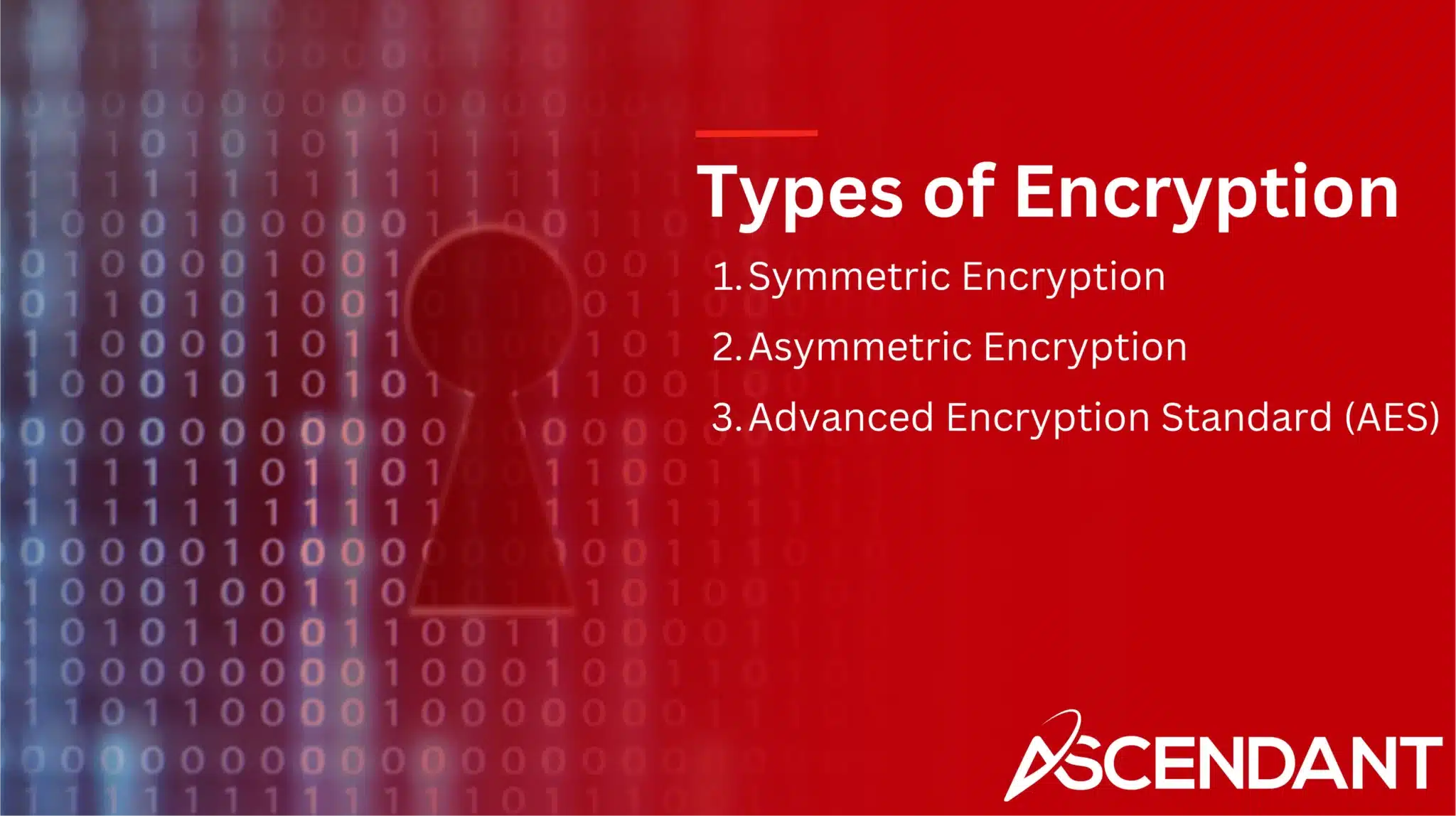
Types of Encryption
Encryption is Classified into three main categories: symmetric encryption, asymmetric encryption, and the Advanced Encryption Standard (AES). These forms of encryption utilize distinct mechanisms to enhance data security.
In symmetric encryption, a singular key serves the dual function of encrypting and decrypting information. Asymmetric encryption operates with two keys—a public key for encrypting messages and a private key exclusively used for decryption. The Advanced Encryption Standard (AES) is recognized as an efficient standard offering robust protection.
Recognizing the differences between these types of encryption aids in choosing the right method for different use cases in order to safeguard information effectively.
Symmetric Encryption
Secret key encryption, also known as symmetric encryption, employs one key to handle both the encoding and decoding of data. This method’s effectiveness hinges on the confidentiality of the key. Once exposed, the encrypted data becomes vulnerable. Symmetric encryption is favored for its efficiency in rapidly securing substantial quantities of information due to its straightforwardness and velocity.
Frequently utilized symmetric algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard), along with Triple DES. The Advanced Encryption Standard stands out for its speed and robust security features, offering various lengths for keys including 128, 192 or 256 bits. Owing to identified weaknesses in DES, making it susceptible to attacks, it has been largely superseded by more secure solutions like AES despite being a pivotal algorithm historically.
Additional significant symmetric algorithms include Blowfish RC4, and Twofish each bringing distinct advantages while ensuring trade-offs are maintained. They all deploy a single secret key during both stages – encrypting and decrypting. As such, intensive focus must be placed on efficient management strategies regarding these keys thus safeguarding sensitive data from unauthorized access.
Asymmetric Encryption
Public key encryption, also known as asymmetric encryption, leverages a pair of keys—a public key for encrypting messages and a private key to decrypt them. This method bolsters security by negating the necessity of exchanging keys over secure channels. Instead, the public key can be shared openly without endangering the confidentiality secured by its associated private key. Asymmetric encryption is invaluable when it’s crucial to maintain protected communications.
Asymmetric cryptographic systems like RSA (Rivest-Shamir-Adleman) and Elliptic Curve Cryptography (ECC) are common tools within this sphere. The former has become a staple in securing transmissions across the internet, while ECC provides comparable levels of security with more compact keys sizes—boosting efficiency. These foundational algorithms underpin numerous protocols dedicated to secure communication such as SSL/TLS, which utilize digital certificates containing these public keys to forge safe connections online.
While boasting greater security advantages than symmetric encryption due largely to its intricate nature, asymmetric encryption calls upon increased computational power for execution. This balance often tilts favorably towards employing enhanced protections, particularly relevant in contexts demanding robust email encryptions or unforgeable digital signatures where safeguarding message integrity and privacy stands paramount.
Advanced Encryption Standard (AES)
Implemented by the United States government in 2001, the Advanced Encryption Standard (AES) is a symmetric encryption algorithm crafted three years earlier. It has risen to international prominence for its strength and performance efficiency. This method processes data in blocks of 128 bits and accommodates keys sized at 128, 192, or 256 bits, providing significant protection that meets diverse application needs.
The combination of potent security features and high operational efficiency positions AES as an optimal solution for encrypting data across various platforms, including both hardware and software systems. Its widespread endorsement by governmental bodies and institutions emphasizes its capability to safeguard sensitive information against unlawful intrusion and cyber threats efficiently.
Common Encryption Algorithms
Encryption algorithms serve as the foundational components of contemporary cryptographic systems. Among these crucial algorithms, one can find:
- RSA
- Triple DES (3DES)
- The Data Encryption Standard (DES), which has been deprecated
- RC4, now deemed insecure and Shunned in modern usage
- AES, which remains a stalwart providing strong encryption across numerous applications.
Understanding these encryption mechanisms is essential when selecting an appropriate method for ensuring robust data security.
RSA
The RSA algorithm is a fundamental element in the realm of public key encryption, playing a vital role in securing internet communications. It operates with two keys—a publicly shared key and another that remains private—to cipher and decipher information, thus ensuring that only the person for whom it’s intended can access the data. Given its resilience to brute force attacks and pivotal function in protecting data transmitted over the internet, RSA is an essential aspect of contemporary cryptographic practices.
In real-world scenarios, RSA doesn’t work alone. Instead, it’s often integrated with additional encryption methods to establish multiple layers of defense. For instance, this key encryption foundation underpins SSL/TLS protocols that safeguard web browsers along with online financial exchanges.
Due to its capability and adaptability within various security contexts, RSA has secured its position as an indispensable ingredient within our arsenal of encryption technology.
Triple Data Encryption Standard (3DES)
Triple DES, also known as 3DES, fortifies the security of the initial DES algorithm through its triple-layered application using three distinct keys. This method significantly expands the key length and boosts resilience against brute force attacks by making unauthorized access considerably more challenging. Despite these enhancements to security, there is a gradual shift away from 3DES toward newer algorithms such as AES due to their superior efficiency.
In situations where modernizing legacy systems to adopt fresher encryption standards proves impractical, 3DES maintains relevance. It serves as an interim cryptographic solution that underscores the relentless progression in cryptography aimed at confronting new and evolving security threats.
Data Encryption Standard (DES)
Initially embraced by the U.S. government in 1977, the Data Encryption Standard (DES) represented an early form of symmetric key encryption that significantly influenced contemporary encryption techniques. With growing computing capabilities revealing its weaknesses, DES was ultimately recognized as inadequate for robust data protection.
The adoption of AES to replace DES signified a major progression towards more resilient key encryption methods designed to counter modern cybersecurity challenges. This evolution highlights the critical need for updating and enhancing data encryption standards continuously to safeguard information against emerging digital threats effectively.
Benefits of Using Encryption
The implementation of encryption is a vital aspect of safeguarding data security, as it plays an instrumental role in preserving the confidentiality of sensitive information. It ensures that only those who are authorized can gain access to critical data, which is pivotal for shielding financial dealings, personal discussions, and proprietary corporate details from unapproved intrusion and digital threats.
Encryption significantly contributes to the preservation of data integrity and authenticity. It employs cryptographic keys as a means to confirm that no modifications have been made to the information during its transmission or storage. This verification process is essential for detecting any tampering attempts and serves particularly crucial in adhering to regulatory standards where keeping intact data integrity is frequently mandated by law.
Committing resources towards advanced encryption methods translates into heightened trustworthiness among consumers while bolstering their confidence in an organization’s dedication to protecting their data. In times where incidents such as unauthorized entries leading to potential leaks could impose hefty costs both financially and reputation-wise on entities involved. Strong preventive measures like encryption act as a fundamental line of defense against these risks associated with unsanctioned access and potential loss of informational assets.
Challenges and Limitations of Encryption
While encryption offers numerous advantages, it also presents various challenges and constraints. The key concern lies in the performance overhead. Engaging in encryption and decryption processes demands extra computational resources that can hamper system efficiency. This may create significant issues for systems requiring rapid data handling and minimal delay.
Another notable difficulty stems from the intricate nature of managing encryption practices. The responsibility to produce, keep safe, and distribute cryptographic keys effectively while ensuring they are regularly updated is a demanding endeavor due to its intricacy. Should these encryption keys be lost or compromised, one might face an irrecoverable loss of data access, which poses a high-stakes threat.
There’s only a fraction of organizations equipped with the capability to decrypt and scrutinize encrypted traffic thoroughly — an essential process for identifying potential concealed threats within it. Striking an equilibrium between stringent encryption measures with their practical deployment and upkeep constitutes an enduring struggle faced by entities across all sectors.
Applications of Encryption
Encryption plays a critical role in numerous aspects of our online existence, ranging from the protection of emails and cloud-stored information to guaranteeing privacy in end-to-end communications. These uses underscore encryption’s adaptability and its vital function in safeguarding sensitive data wherever it may reside.
To explore Consider key examples such as email encryption, encrypting data stored on the cloud, and implementing end-to-end encryption methods.
Email Encryption
The practice of securing email content through encryption is critical for maintaining the privacy and integrity of communication via email. Utilizing well-regarded protocols such as PGP (Pretty Good Privacy) and S/MIME (Secure/Multipurpose Internet Mail Extensions), these methods afford varying degrees of security that guarantee only authorized recipients are able to decipher encrypted messages, thus shielding sensitive data from unauthorized exposure.
Organizations often leverage sophisticated enterprise-level email encryption solutions that integrate potent encryption algorithms designed to meet specific organizational requirements. Equipped with functionalities like sender-based encryption and a variety of key management systems, these robust solutions offer an extensive layer of defense for corporate communications. The use of symmetric algorithms like Blowfish and Twofish is common in this context due to their efficiency and adaptability, which bolsters the overall security measures applied to emails.
By encrypting electronic mail correspondences, companies can not only ensure confidentiality within their interactions, but also adhere to various regulatory mandates while averting potential data breaches. This proactive measure preserves confidential information confidently between parties involved, thereby building trust among clients and business associates alike.
Cloud Encryption
Securing data in cloud environments is imperative, which makes cloud encryption a crucial process. By encrypting data prior to its upload to the cloud and making it unreadable without corresponding decryption keys, this method safeguards sensitive information from illicit access even if there’s a breach in the cloud storage security. Encryption as a Service (EaaS) presents an attractive model that works on pay-as-you-go terms, providing organizations with flexible options for managing their encryption requirements without substantial initial costs.
For those enterprises seeking heightened oversight of their encryption strategies, the Bring Your Own Encryption (BYOE) approach serves well. BYOE enables companies to utilize personal encryption keys and algorithms they trust, thus fortifying security measures and governance over stored data. This practice is particularly advantageous for entities faced with rigorous standards for data protection. It assures them that their critical information maintains its confidentiality within the boundaries of cloud computing platforms.
End-to-End Encryption
End-to-end encryption (E2EE) guarantees that only the designated recipients have the ability to decipher message contents, offering strong protection and confidentiality. In systems employing E2EE, entities like Internet Service Providers (ISPs) lack the capacity to unlock these encrypted messages, which safeguards against illicit access and tampering. This encryption technique is extensively implemented across various platforms including messaging apps, email services, and additional forms of communication tools to secure sensitive data.
The application of E2EE is particularly crucial in situations where maintaining data privacy is critical—this includes legal discussions, monetary transactions, and private communications. By encrypting information from the origin point all the way through to its destination recipient’s device, E2EE ensures a protected pathway for communication thus shielding personal details from interception or unwanted breaches.
Key Management in Encryption
Safeguarding encrypted data requires meticulous management of cryptographic keys, which includes their secure creation, storage, renewal, and disposal. Properly handling these keys helps prevent them from falling into the wrong hands or being used repeatedly, thereby minimizing the threat of unauthorized access to sensitive information and incidents of data breaches. Security apparatus such as Hardware Security Modules (HSMs) bolster key management security by offering a dedicated protected space for both storing encryption keys and performing related activities.
The protection afforded by encryption is heavily dependent on how securely decryption keys are stored since they must be kept out of reach of potential intruders. Given that modern encryption often uses complex algorithms generating extremely long strings for these keys—ranging in length from hundreds to thousands of characters—it underscores the importance of implementing robust systems for managing these critical assets effectively. Organizations can take advantage of approaches like Bring Your Own Encryption (BYOE), giving them more control over their particular methods employed in encrypting data and overseeing their own cryptographic key operations.
Thorough management practices not only defend against threats to encrypted datasets, but also help organizations meet various regulatory standards set forth for ensuring comprehensive data security measures are upheld. Routine cycling through different sets of encryption keys along with organizing those based on specific roles within systems or according to stages within their individual lifecycles remains a cornerstone strategy in preserving an infallible framework around securing encoded communications or stored files.
Detecting Encrypted Threats
The task of identifying threats within encrypted traffic is fraught with difficulties, mainly because decrypting all the traffic requires substantial effort and time. Enterprises have the option to pour resources into sophisticated tools like big data analytics, machine learning algorithms, and network behavior analysis that can pinpoint subtle signs and odd patterns which could indicate a lurking threat. By doing so, companies are better equipped to take swift action against potential dangers.
Employing machine learning combined with network analytics proves especially potent for sifting through encrypted threats as these technologies excel at scrutinizing inconsistencies and trends without delay. Such capabilities significantly bolster an organization’s defenses by safeguarding sensitive information from intricate cyber-attacks.
Pouring funds into these innovative solutions is crucial in upholding stringent data protection standards amid a digital domain where encryption prevails more than ever before. This fortifies organizational measures to shield their precious data effectively.
Summary
Encryption serves as a formidable defense mechanism for the security of sensitive data, playing an essential role in maintaining the privacy and protection against unauthorized interference. The process entails transforming readable plaintext into unintelligible ciphertext to prevent unwanted access or cyber threats. It is imperative to have knowledge of different encryption types such as symmetric cryptography, asymmetric algorithms, and Advanced Encryption Standard (AES) to choose suitable encryption techniques for distinct security requirements.
Despite potential challenges like its impact on system performance and intricate key management issues, encryption remains a fundamental element in contemporary data protection strategies. Organizations that dedicate resources towards advanced encryption methods coupled with efficient practices for managing keys can significantly fortify their defenses against breaches while achieving compliance with legal standards and gaining consumer confidence. Given the perpetual advancement of cyber dangers, encryption’s significance is destined not only to persist but also increase within our increasingly digital existence.
 Frequently Asked Questions
Frequently Asked Questions
What is encryption, and why is it important?
Encryption converts accessible data into a coded structure, which cannot be understood without the proper decryption key. This process is vital for protecting sensitive information, maintaining confidentiality, and keeping online transactions secure.
How does symmetric encryption differ from asymmetric encryption?
Asymmetric encryption uses two different keys for encryption and decryption, which increases security but also demands more computational power. In contrast, symmetric encryption relies on the same key to perform both functions.
When deciding between the two types of encryption methods, one must weigh the need for stronger protection against the necessity for system performance efficiency.
What are the benefits of using encryption?
Encryption provides critical benefits such as data confidentiality, integrity, and sender authentication, while also enhancing regulatory compliance and protecting financial information.
This ultimately fosters greater customer trust in the security of their data.
What are some challenges associated with encryption?
The implementation of encryption introduces obstacles, which include a decline in performance owing to increased processing demands, intricate procedures for setting it up and substantial complexities associated with managing keys.
Should the encryption keys be misplaced or lost, there is a risk that data may become irretrievably inaccessible.
How can encrypted threats be detected?
Encrypted threats can be effectively detected through the use of big data tools, machine learning, and network analytics, which can flag obscure indicators and behaviors for a proactive threat response.
Implementing these technologies is essential for enhancing security measures in an increasingly complex digital landscape.