A firewall is your organization’s first point of defense against cyberattacks. However, choosing the right type of firewall for your business can be challenging.
Learn More About Network Security
You may be wondering how firewalls work, the different types of firewalls and how to choose the best for your organization. In this article, we take you through what a firewall is, how firewalls work, how firewalls differ from other security devices, the different types of firewalls and how to make the best firewall buying decision for your organization.
By the end of this article, you’ll be able to define firewall and understand which type fits your unique business needs.
In This Article:
- What Is a Firewall?
- How Does a Firewall Work?
- How are Firewalls Implemented?
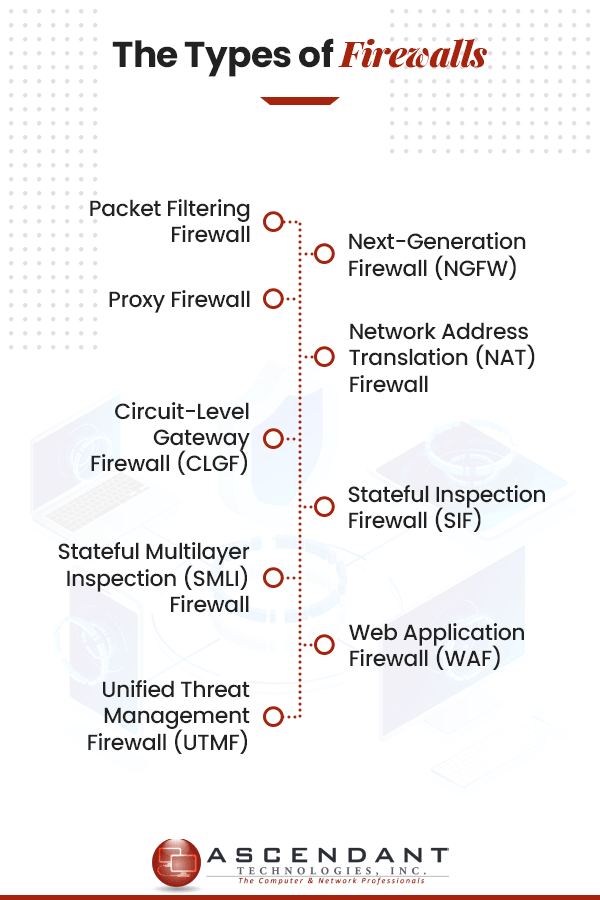
- Types of Firewalls
- Packet Filtering Firewall
- Next-Generation Firewall (NGFW)
- Proxy Firewall
- Network Address Translation (NAT) Firewall
- Circuit-Level Gateway Firewall (CLGF)
- Stateful Inspection Firewall (SIF)
- Stateful Multilayer Inspection (SMLI) Firewall
- Web Application Firewall (WAF)
- Unified Threat Management Firewall (UTMF)
- Do All Businesses Need a Firewall?
- Contact Ascendant Technologies for Firewall Services
What Is a Firewall?
A firewall is a security device — either physical, software or virtual— that tracks outgoing or incoming traffic from a device, an application or a private network. The firewall either accepts or denies data packets — the unit with which data is transmitted— based on how it’s configured.
Firewalls act as a barrier between traffic from public networks, such as the internet, and a private internal network, such as your company’s private network, applications, website or devices.

A firewall is different from other security solutions such as antivirus software, routers, proxy servers, Intrusion Prevention Systems (IPS) and a virtual private network (VPN). The difference is in what firewalls do and how firewalls work.
How Does a Firewall Work?
Because firewalls protect your system against attacks, they are placed across network connection points so they can analyze every data interchanged between the networks.
A firewall protects your internal private network — sometimes called your network perimeter — from attacks by constantly analyzing traffic trying to go through your network’s entry points — called ports. Based on the rules that you set, the firewall allows or blocks data packets.
What Is a Firewall Rule?
A firewall rule is a set of control instructions you provide to a firewall at the device level or organization security policy level that determines the traffic that is allowed or denied.
What Makes Up the Firewall Rule?
Fundamentally, firewall rules consist of a source IP address, a destination IP address, a destination port number and a protocol. While this is on the very basic level, some firewalls implement other technologies that analyze and inspect the content of incoming traffic, monitor them throughout the network and create patterns to understand harmful traffic.
What Is a Port, Protocol and IP Address?
Ports are the points in your network where connections start and end. Ports control how your network and devices interact with other networks. A protocol is how the data is sent and received — for example, HTTP is the protocol for communication on the internet — and an IP address is a unique address that digital devices use to send and receive data in a network.
Imagine the firewall as the security agent at the gate of your company’s building and the firewall rules as the instruction you give to the security agents on whom to allow into the building.
Based on your organization’s security policy, you could instruct your security agents to only allow people who dress corporate (source IP address) and drive a Toyota (protocol) into your organization (destination IP address) and deny everyone else. Once they’re in, your guests are allowed in only to certain offices in your organization (port numbers).
Firewalls can work in two extremes. Based on the pre-defined firewall rules, firewalls can either allow traffic from a list of trusted IP addresses and drop all other traffic or deny traffic from a given list of IP addresses and allow all other traffic.
But that’s not all. Once the data packet is inside the network, firewalls can still monitor their interaction with your system and control where they can access your network. For example, proxy firewalls can restrict access to certain pages on a website or web application.
Now, this is very important. Different firewalls provide different levels of security. To ensure complete security, you may have to implement a multilayered firewall architecture, which uses different firewalls together to combine their functions.

How are Firewalls Implemented?
Firewalls come as either software, hardware or cloud-hosted:
- Hardware firewalls: Also known as network-based firewalls, hardware firewalls are physical gateway security devices that are integrated inline into your network connection. They can be complex to use but have the advantage of not consuming your existing system resources such as RAM or CPU power.
- Software firewalls: Software firewalls are installed into each device, such as computers, routers or servers, that they need to protect. They run on existing system resources like CPU and RAM of the devices they are installed in. Software firewalls are also known as hosted firewalls, and they provide precise control over the traffic within the device and from outside the device.
- Cloud-based firewalls: Also known as firewalls as a service or virtual firewalls, this type is hosted on the cloud and connected to a network or device to monitor incoming and outgoing traffic. They are used in cases where installing a physical or software firewall is difficult. For example, managed service providers (MSP) use cloud-based firewalls for the businesses they offer IT services to.
Using a virtual firewall doesn’t require a physical device or installing software. The firewall is connected to your system from the cloud and monitors internal communications as well as communication from external domains. How you set up your firewall rules and the level of security your firewalls provide depends on the type of firewall you purchase and implement for your organization.
Types of Firewalls
Below you’ll learn how the nine different types of firewalls work and the level of security they can provide your company. We also point out some of the benefits and drawbacks of each firewall to help you decide which firewall to implement. Let’s dive in!
1. Packet Filtering Firewall
Packet filtering firewalls are usually placed at the intersection of your network and an external public network, such as the internet.
They provide surface network security by examining the headers — basically the source and destination IP addresses — of incoming data packets and allow or deny access based on pre-defined security rules.
Some packet filtering firewalls gather information on each data packet and remember it when any new data packet arrives, while some packet filtering firewalls analyze data packets independently of one another.
There are some disadvantages to using packet filtering firewalls. Packet filtering firewalls offer very basic protection and can be easy targets for attackers. This is because they only analyze the data headers and do not go into the content of the packet. This means a trusted source can be used to send malicious data that can corrupt your customer or business database.
On the other hand, packet filtering firewalls are easy to implement. They can also act as a basic level of security for the entire network for businesses with little traffic or where serious attacks are not expected.
2. Next-Generation Firewall (NGFW)

Analyzing the content of the data packet provides an added level of security that stops malicious data transmitted via trusted sources and protects your system from attacks. This comes in handy for businesses in the health care industry and any business where customer data privacy is crucial and attacks are high.
NGFW firewalls include more security devices to the basic security layer of conventional packet filtering firewall products. Additional security devices can include deep packet inspection, intrusion prevention systems, encrypted traffic inspection and antiviruses. This makes next-generation firewalls an extra secure firewall type.
There are some challenges with the next-generation firewall. The extra components of the next-generation firewall also mean an increase in complexity and cost. This can make installing a next-generation firewall more costly for small and mid-scale businesses that may not have a huge budget to spend on firewalls.
3. Proxy Firewall
Also known as the application-level firewall, the proxy firewall controls traffic transmitted through the FTP and HTTP protocols.
The proxy firewall offers security for communication via the internet and at the application layer. The proxy firewall analyzes traffic requests sent to the system application and allows or denies entry based on the existing rules using both stateful and deep packet inspection.
Here’s the benefit of using a proxy firewall. Proxy firewalls provide fine-tuned and specific control over network access to incoming traffic. For example, the proxy firewall can provide access to a website and restrict access to certain pages based on the rules laid out. This helps to ensure important data is not accessed by hackers from within the firewall and provides maximum security.
Here’s how proxy firewalls work. Proxy firewalls are delivered via the cloud. They prevent a direct connection to your system by first establishing a proxy connection with external devices or networks that want to communicate with your network. This allows the proxy firewall to inspect the data that wants to be transmitted to ensure its legitimate before connecting it to your network.
However, there is a downside to the proxy firewall. The added step in the proxy connection introduced by the proxy firewall makes the connection slow. Also, proxy firewalls may be expensive and their negative impact on your connection speed can affect your overall network performance.
4. Network Address Translation (NAT) Firewall
A network address translation firewall allows different devices with different IP addresses to access the internet using one IP address. This helps to mask the IP address of all the individual devices and presents one IP address for interaction with the public network.
When you send data or communicate in a network, your devices do so using their IP addresses. To launch an attack against any system, attackers scrape for the IP addresses of the system. If an attacker wants to send malicious data to your network or to a particular device in your network, they’d use the device’s IP address to launch the attack.

Small and large-scale businesses can increase the security of their devices connected to the internet using a network address translation firewall.
Also, businesses that run on the internet can secure their operations and reduce the risk of cyberattacks with a network address translation firewall. A network translation firewall can help boost the security of your employees’ operations, especially now, when more companies are working remotely.
5. Circuit-Level Gateway Firewall (CLGF)
Circuit-level gateway firewalls ensure connections between your network and remote devices are legitimate and secure.
That is, when a device in your network creates a connection with a remote device, the firewall makes a virtual connection on behalf of the device to ensure the internal device is secure and its identity is masked. Even after the connection is established, the circuit-level gateway firewall monitors the session and data exchange.
However, circuit-level gateway firewalls do not inspect the content of the connection, they only analyze the legitimacy of the TCP handshake, which is the process that sets up the connection between your device and the external network. This means malicious data can be passed through a legitimate connection into your system.
That is why circuit-level gateway firewalls are not used alone. Instead, they are used as part of a multilayered security architecture for better network protection. For example, you can combine a circuit-level gateway firewall with any firewall device that offers deep packet analyses of the incoming data.
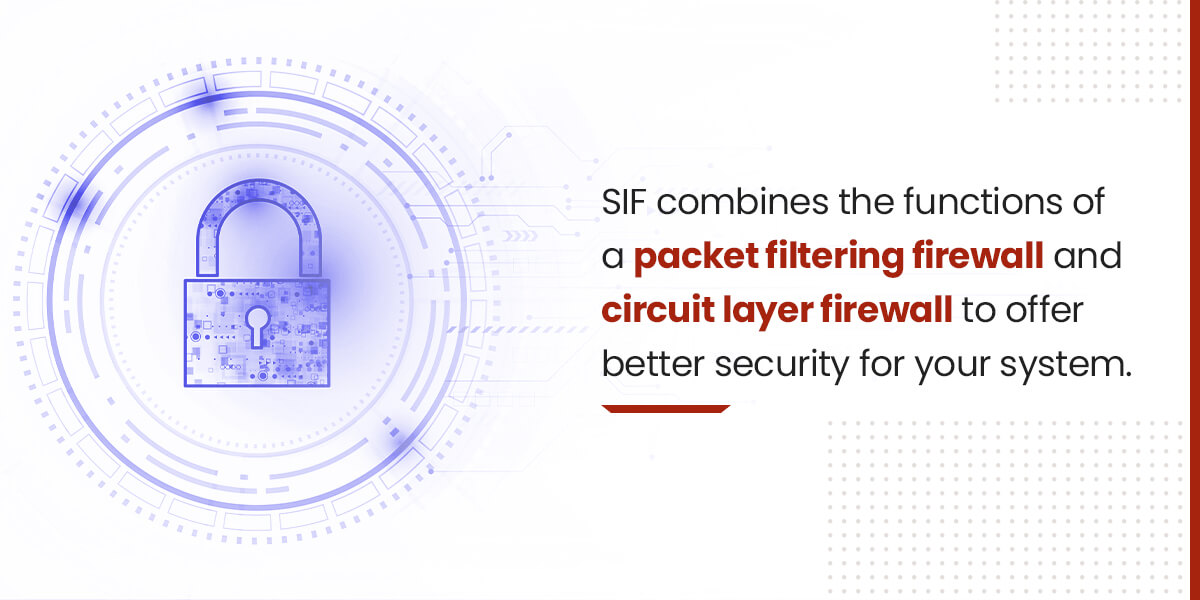
6. Stateful Inspection Firewall (SIF)
Stateful inspection firewalls provide consistent monitoring of data packets in the network. The stateful inspection firewall analyzes the headers and content of a data packet and determines if it’s part of a connection or an already established session in the network.
7. Stateful Multilayer Inspection (SMLI) Firewall
As the name implies, a stateful multilayer inspection firewall inspects the headers of data packets, monitors their state across different layers of communication and keeps track of established connections.
Stateful multilayer inspection firewalls inspect data across the network, transport and application layers. SMLI also inspects the content of each data packet to ensure they’re from trusted sources and the data contained is harmless to the system based on pre-defined firewall rules and known trusted sources.
Because of the stateful and multilayer inspection provided by stateful multilayer inspection firewall, they help promote the security of your network every step of the way. However, these extra security features can negatively affect the functionality of your system and slow down its performance.
8. Web Application Firewall (WAF)
Web application firewalls are designed to provide network security to a website or web application. WAF offers network monitoring and gateway security for traffic moving in and out of a web-based application or website at the application and web layer. They can be either physical, cloud-based or provided as a plugin in a server
9. Unified Threat Management Firewall (UTMF)
A unified threat management firewall combines the security services and features of different firewalls into one firewall solution.

Do All Businesses Need a Firewall?
If you’re wondering whether your office really needs a firewall, the answer is yes. Businesses of all sizes are open to attack, including small or mid-size businesses.
Two in every three small and medium-scale businesses experienced a cyber attack in 2020. In the United States, the figures are higher. And the cost of a single data breach to an SMB is $149,000
Installing a firewall can help you secure your system and ensure smooth operations. The type of firewall you deploy for your business depends on your budget, network operations, what you need to secure and your entire system architecture.
It is good practice to have a physical firewall as your first front of defense before adding different layers of software or cloud-based firewalls. Software firewalls only filter traffic that has already entered your network. This is because they run on your resource, unlike hardware firewalls that are independent and can filter the traffic entering your entire network.
Also, consider installing a combination of firewalls for maximum security. Where one firewall lags, the other will cover for it. Most managed service providers use cloud firewalls to offer virtual firewalls for businesses. In some cases, this is in addition to existing security systems already in place.
Installing a security system can be expensive, but not as expensive as a hack and the effect it will have on your business data and operation, employee workflow and reputation. To help you make the best choice, you can work with a security expert who can help you determine the firewall that suits your business needs.
Contact Ascendant Technologies, Inc. for Firewall Services Today
Choose Ascendant Technologies, Inc. If you want expert advice on which firewall to install for your business. When you reach out to us, we offer you a free network assessment to help you figure out where the loopholes are in your network security and where to start fixing the cracks.
We are an outsourced managed IT provider with an active team of experienced professionals ready to meet your business’s needs. Our IT management strategy can save you time, fortify your it infrastructure and let you enjoy all the benefits of a dedicated IT team for a fraction of the cost of hiring an in-house IT team. We provide simple, cost-effective solutions to help you secure your company’s data.
We bring over 25 years of IT support for companies in the tristate area and partner with trusted companies like Microsoft, Nextiva, Datto, Sonicwall and Fortinet. Reach out to us today to get started building the best firewall for your unique needs.