Hackers have a vast toolkit, thanks to the recent rise of generative artificial intelligence models and the increasing popularity of third-party software-as-a-service technologies. Social engineering attacks like phishing now happen more frequently — and they’ve become highly sophisticated due to these technological advances.
Knowing what to look for and how to respond is crucial to prevent severe losses and damage from social engineering.
What Is a Social Engineering Attack?
Social engineering perpetrators use psychological tactics to manipulate targets into completing specific actions, such as:
- Divulging sensitive information
- Sending money to fraudulent accounts
- Downloading malware onto their computer
- Providing unauthorized access to secure areas or networks
A social engineering attack usually involves four stages.
- Preparation: A cybercriminal collects information about your organization, such as the behaviors of specific employees or groups, to strategize their attack.
- Infiltration: The attacker engages with their target, attempting to intimidate or gain trust. For example, the victim might receive a phishing email from a sender that looks like it is from a high-ranking company executive, but is actually the attacker’s clever spoof of that person’s email address.
- Exploitation: Once the criminal gains access to your system, they launch the full attack, which could include anything from exfiltrating sensitive data to siphoning money from company bank accounts.
- Exit: Once the attacker has what they want, they disappear from your network without leaving a trace behind.
These attacks can cost your organization millions or even billions in losses, reputational damage and downtime. Proactively stopping as many attacks as possible is the best way to protect your company from harm.
Typical Social Engineering Attacks
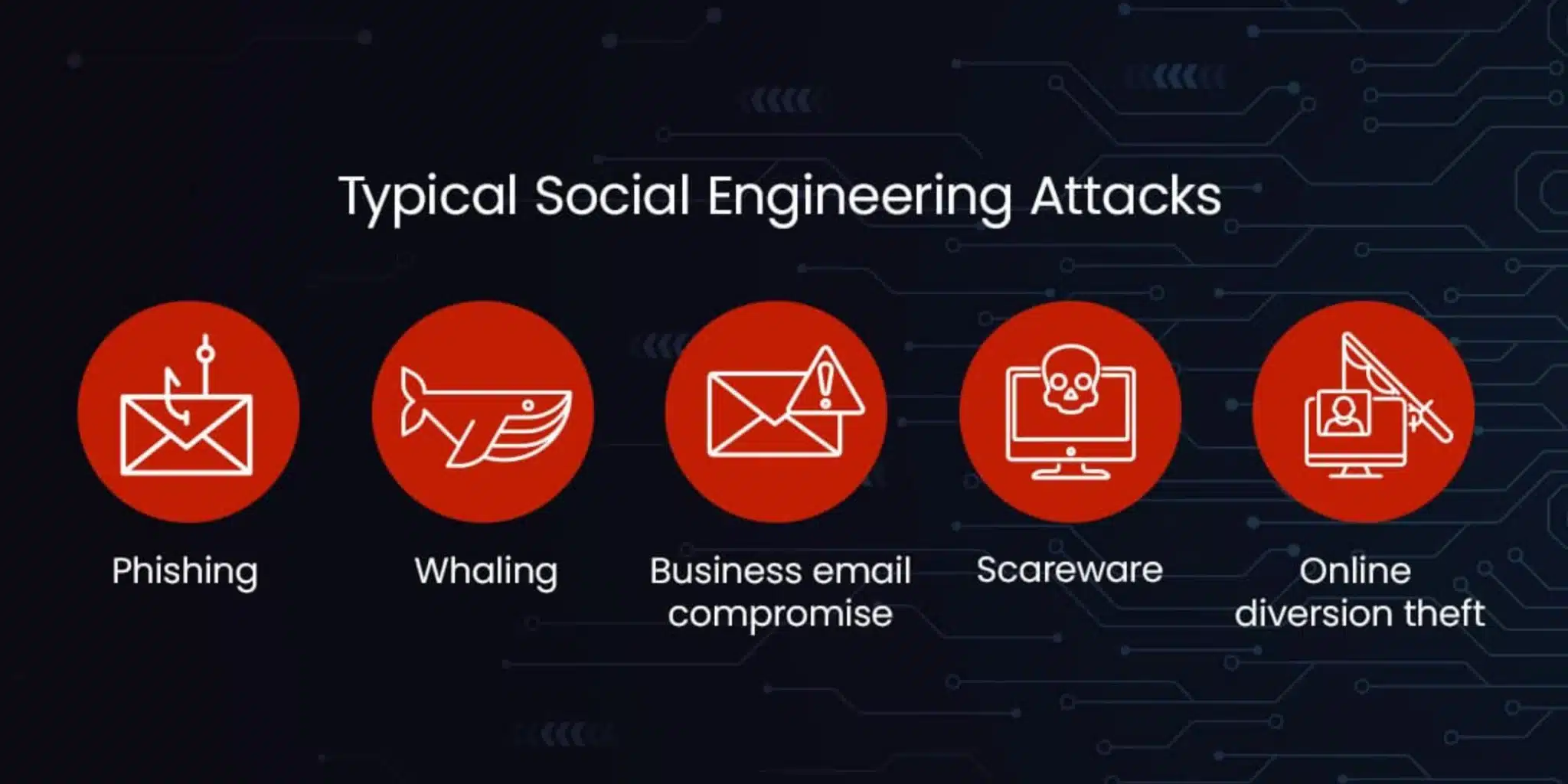
Social engineering scams may include the following.
- Phishing: The attacker sends fraudulent emails that seem to be from a reputable source, tricking the recipient into doing their bidding. Most people are familiar with this tactic because it’s easy and low-effort for criminals to perpetrate.
- Whaling: Whaling attacks take phishing to a new level by spoofing high-level members of your organization, such as your C-suite executives, and sending fraudulent messages to your employees asking them to perform a specific action.
- Business email compromise: The attacker gains access to a legitimate business account — such as an external vendor, customer or employee — and uses it to convince others within the organization to share company secrets or send them money.
- Scareware: The attacker startles users with loud, flashy pop-ups that tell them they have a computer virus and trick them into downloading a fraudulent antivirus solution to get rid of it. Once the user installs the software, the attacker gains access to the network and either steals sensitive information or installs real malware on the device — or both.
- Online diversion theft: The attacker tricks their target into sharing or sending information to the wrong people, usually by spoofing a colleague’s email address.
Social engineering also goes beyond cybercrime. For example, a tailgating attack is when an unauthorized person follows closely behind their target to sneak into a secure area — or tricks the victim into letting them in.
High-Profile Social Engineering Attack Examples
Even household names with bleeding-edge cybersecurity tools have fallen prey to social engineering hacks. Here are some noteworthy case studies from the past decade.
2013-2015 — Google and Facebook Wire Fraud Attacks
Lithuanian hacker Evaldas Rimasauskas carried out the most extensive social engineering attack ever committed against tech giants Google and Facebook from 2013 to 2015.
Masquerading as representatives from an external IT vendor, Rimasauskas and his collaborators sent legitimate-looking invoices to specific company employees, billing them for purchases they had supposedly made from real-life vendors. Upon receiving the funds, Rimasauskas redirected them into fraudulent accounts all over the world.
In the end, these hackers managed to steal more than $120 million — and even after Rimasauskas received a five-year prison sentence in 2015, the companies only recovered half their losses.
2022 — Uber and Rockstar Games Slack Attacks
In early September 2022, an unauthorized user named “TeaPot” gained access to Uber’s internal Slack channel and announced their presence as a hacker. The subsequent investigation revealed that the hacker had managed to infiltrate the system by pretending to be a corporate IT expert and tricking an employee into sharing the credentials for Uber’s company VPN.
In 2022, Rockstar Games experienced a similar attack from the same hacker. Though the attack’s details remain unknown, TeaPot claimed to use the same social engineering tactics as in the Uber breach.
How to Spot a Social Engineering Attack
While social engineering scams can be devastating, you and your team can proactively identify and prevent them if everyone knows what to look for.
- Excessive emotion: Scammers try to appeal to their target’s feelings to manipulate them into risky actions. Threats are a frequent tactic, though attackers also exploit emotions like guilt, curiosity or even excitement to get what they want.
- Sense of urgency: Hackers often put a time limit on their demand, pressuring their victim to act impulsively.
- Unexpected interactions: If an employee suddenly receives an email from an account they usually don’t correspond with — such as a C-suite executive or someone outside their department — that message should raise red flags.
- Abnormal behavior: Though the hacker likely has an idea of who they’re impersonating, their messages often seem unnatural or out of character. Watch for unusual messages, misspellings, awkward phrasing and uncharacteristic requests.
- Suspicious links or attachments: Employees should always check that links and attachments are secure before opening them, as these are the most frequent ways hackers gain access to corporate networks. Hovering the cursor over links to check their destination and using technologies like intrusion prevention systems can identify and eliminate malware before it can affect you.
- Grammar and spelling errors: Poor grammar is a dead giveaway for social engineering messages, though generative AI chatbots have made it easier for scammers to produce more convincing communications with minimal effort.
Staff training programs can help employees learn to recognize these signs and teach them how to respond, significantly reducing your risk of a breach.
Enhance Your Security Posture With Ascendant Technologies
You can quickly eliminate social engineering attacks and protect your organization when you arm yourself with knowledge and tools. That’s where Ascendant Technologies comes in. As a top-ranking managed IT services provider, we give our clients access to solutions and expertise from New Jersey’s best cybersecurity consultants — plus, we can train your staff so they know what to look for.
Arm your employees against social engineering scams. Contact us today to set up a discovery call with our team.


