No sound on computer? Get your audio back with simple solutions to fix common problems and get your sound working again.
Windows 11 update failed? Identify common reasons why updates fail and how to troubleshoot issues to successfully complete your system update.
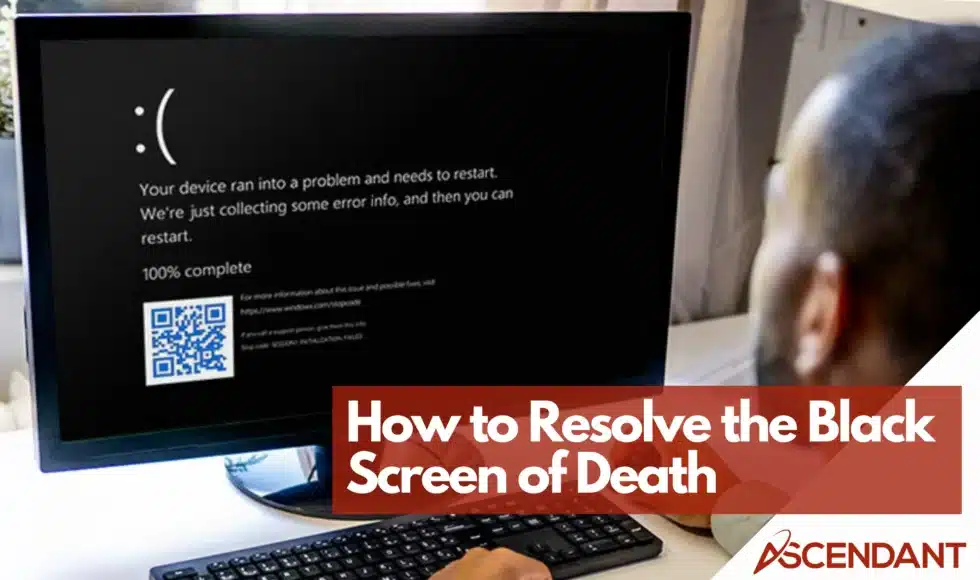
Black screen of death can be frustrating, but there are ways to fix it. Learn what causes it and follow these steps to get your screen working again.
How to find IP address on Mac quickly and easily. Follow simple steps to locate your local and public IP address using built-in tools and settings.
How to factory reset MacBook Pro safely—erase your data, sign out of accounts, and reinstall macOS. Get step-by-step instructions to reset your Mac.
Clear cookies to remove stored data, improve privacy, and fix website issues. Learn how to do it on any browser in a few simple steps.
Colocation pricing can vary widely based on your needs. In this guide, we break down the costs of space, power, and bandwidth so you can plan your budget accordingly. In This Article: Key Factors Influencing Colocation Pricing Additional Costs in Colocation Services Real-World Examples of Colocation Pricing Evaluating Colocation Providers Hidden Fees to Watch For […]
Types of penetration testing help uncover security gaps before attackers do. See which tests matter most for protecting your network.
Cybersecurity protects systems, networks, and data from digital attacks. These attacks aim to steal, modify, or destroy sensitive information. In this article, we will delve into key types of cybersecurity, the evolution of cyber threats, and the latest cybersecurity trends. In This Article: Key Types of Cybersecurity The Evolution of Cyber Threats Cybersecurity Trends in […]
WiFi keeps you connected, but how does it actually work? Click to find out the technology behind wireless internet and what makes it so fast.