Privilege Escalation is a quiet but serious threat. Find out how it’s used, what makes systems vulnerable, and how to reduce your risk.
Cyber hygiene plays a major role in staying secure. Learn easy, everyday practices that make a real difference in your digital safety.
Trojan virus infections can hide in plain sight. Learn how they spread, what damage they cause, and how to keep them out of your system.
Pharming attacks trick users into giving up sensitive data. Learn how these threats work, how they spread, and what steps you can take to stay protected.
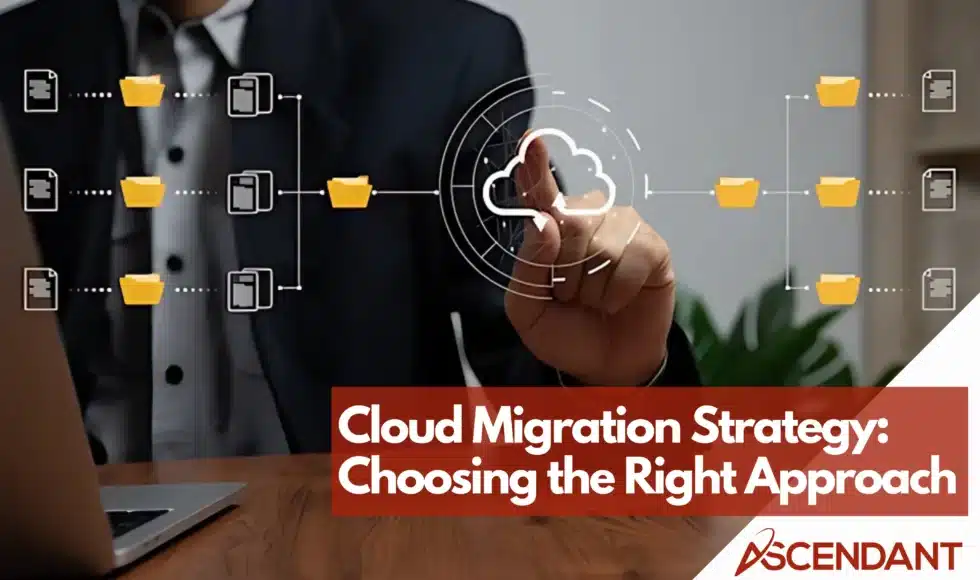
Cloud Migration helps businesses transition to the cloud safely. Choose the best approach to ensure minimal downtime and secure data transfer.
Mesh Network improves WiFi speed and coverage, eliminating dead zones in your home or office. Find out how it provides better connectivity.
Threat modeling allows you to analyze potential security risks before they become threats. Strengthen your defenses with a structured approach to cybersecurity.
Linux on Mac: Find the best methods to install Linux on your Mac with simple steps and guidance for an easy setup.
Logic bomb attacks don’t always show signs right away—learn what makes them dangerous, where they show up, and how to stay one step ahead.
Domain controller tips you actually need—walk through real scenarios, quick checks, and fixes that help keep your systems moving without the guesswork.